Nowadays, we heard the word cyberattack, cybercrime, cyber security so what actually do these all terms mean? In this blog, you can learn all about it.
Topic to be covered :
- What is Cyber Security?
- Importance of Cyber Security
- Types of Cyber Attacks
- Layers of Cyber Security
What is Cyber Security?
Cyber Security is a field where cyber security experts secure the system, network, program, IoT device, some time hardware also.
Cyber is the process or technology to protect and secure the system, network, software, device, or hardware components.
In another word, Cyber is the term that relates to system, program, network, or data and Security is related to the protection of all cyber terms.
Further, Cyber Security is used in many categories that are :
- Network Security
- Cloud Security
- Application Security
- Information Security
Importance of Cyber Security
Cyber Security is the field that protects the data and privacy of the user, organizations, banking, and financial data.
Cyber attacks can be heavy expensive for businesses and sensitive data companies.
Cyber attacks can also damage the reputation of companies or organizations.
Nowadays cybercrime and attack get more wildly spread and very harmful for society. Cyber Criminals enable to get access in many ways.
So for awareness about cyber security, some organizations like GDPR set examples where you can know all information about cyber laws, security, and IT sections.
You can also read about different programming languages
Types of Cyber Attacks
Cyber attacks are an attempt to destroy, damage, steal, reveal the data of a system or program, or network and that impact on their privacy. There are some common types of attack which are used many times and most common time.
DoS and DDoS Attack
DoS means Denial of Service and DDoS means Distributed Denial of Service. It makes the system to unaccessible to authorized persons. It achieves by sending too much traffic or unusual data to the client. This attack is also used to create vulnerabilities.
Ransomware Attack
Ransomware attack happens when an attacker or hacker locks or to be hostage the system of the victim and demands money or some sensitive data and then after getting rewards it unlocked the system.
Ransomware attacks enter the system multi-way like email, malware, websites resources.
Password Attack
Most of the time people set the same password on multiple platforms on some notes and files on the computer. At that time attacker can get passwords via sending malware. Password attacks get through two methods as brute force attack and dictionary attack. In a brute force attack attacker applied one by one character to the password and hacked it. In another dictionary, the attacker applied a string of dictionaries and hacked the password.
To protect the password follow some tips :
Change password in regular interval
Set more complex passwords like used characters, numbers, symbols.
Avoid autosave passwords in any browser if possible
MITM Attack (Men In The Middle)
It is a kind of attack that permits a hacked to catches among client and server and create a bridge between them. Because of this, the attacker will actually want to read, edit or modify and change messages between client and server.
Phishing
Phishing is attacker sends an email that has some malware or virus or worms that the user understood is an actual email and clicks some link on that will create malicious acts in the system and then damage or remove data.
To protect the system do not click on some random email, first, check the mail and verify that after that click on some links.
SQL Injection Attack
SQL injection attack possible when website or program or software which is dependent on the database to the server. In that attacker can get all information about database and users data.
Trojan Horse Attack
Trojan Horse attack happed when the user by mistake executes the innocent program and runs it then malware inside the trojan can enter via a backdoor to the system. And then it can damage the system or data privacy. To prevent to do not download or install any malicious program.
Also, there are many more attacks that can be damaged systems. You can get information on google about it.
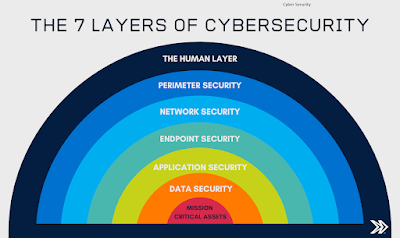
Layers of Cyber Security
Total 7 layers of cyber security that can protect the mission-critical situation.
In this the data that we have to protect
Data Security
This can protect the transfer and storage of data
Application Security
Application Security protect access to an application, an application’s access to your mission-critical assets, and the internal security of the application
Endpoint Security
Endpoint Security protects the endpoint connection between device and network.
Network Security
Network Security protects the network from unauthorized persons or access.
Perimeter Security
Perimeter Security protects control of physical and digital security methods of business model.
The Human Layer Security
Human security is the most important in this. The human can easily break all security of the organization security.


0 Comments